Configuring a Primary Domain Controller to Use DHCP in a Test Lab
- Posted by
- Posted on January 11, 2026
- Servers,Virtualization,Windows
- No Comments.
In production environments, domain controllers are almost always configured with static IP addresses. However, in test and lab environments, it is sometimes desirable to allow a primary domain controller to obtain its IP address via DHCP, such as when running inside virtualized lab setups. We will walk through a real troubleshooting scenario where a Windows […]
How to Fix the “Your Organization Manages Updates” Error in PC Health Check
- Posted by
- Posted on January 6, 2026
- Computers,IT Support,Microsoft Applications,Windows
- No Comments.
Fixing the “Your Organization Manages Updates” Error in PC Health Check When running Microsoft’s PC Health Check app, some users encounter a misleading warning stating that updates are managed by their organization. This message can appear even on personal or standalone systems that are not joined to a domain, not enrolled in MDM, and […]
Troubleshooting Windows Boot Failure: Error 0xc000000f
- Posted by
- Posted on January 5, 2026
- Computers,IT Support,Windows
- No Comments.
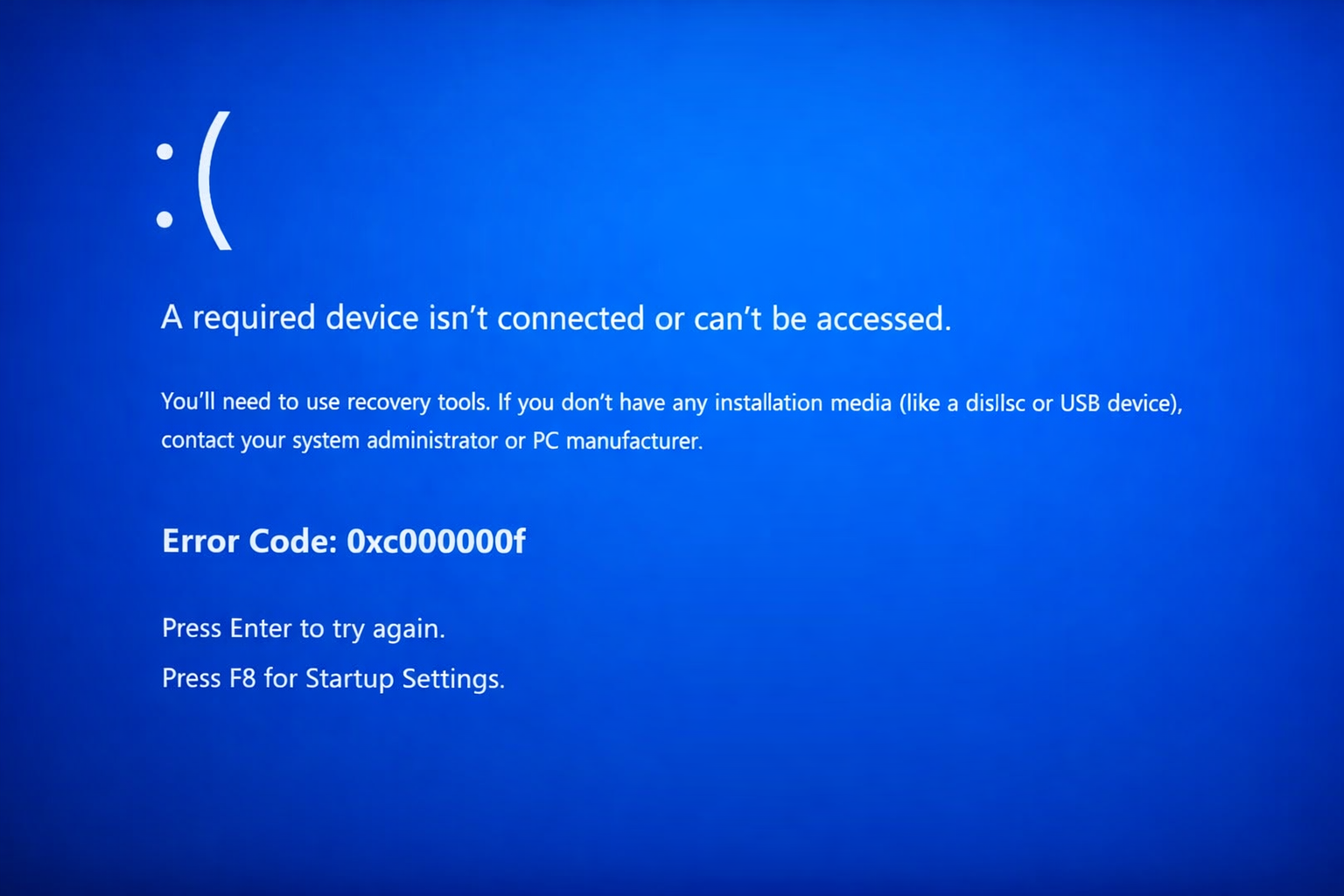
Fixing Boot Error 0xc000000f “A required device isn’t connected or can’t be accessed.” OverviewWindows A system that fails to boot and displays the blue screen error 0xc000000f is unable to locate or access the required boot device. This error commonly appears during startup before Windows loads and prevents the operating system from launching. This issue […]
adsiedit.msc vs dsa.msc: Two Active Directory Tools Every Admin Should Understand
- Posted by
- Posted on December 16, 2025
- Computers,IT Support,Microsoft Applications,Servers,Windows
- No Comments.
adsiedit.msc vs dsa.msc: Two Active Directory Tools Every Admin Should Understand If you manage Active Directory (AD), you will eventually encounter two long-standing Microsoft management consoles: adsiedit.msc (ADSI Edit) dsa.msc (Active Directory Users and Computers, commonly called ADUC) Although they both interact with the same directory, they serve very different purposes. One is designed for […]
Restore Legacy Print Que in Windows 11
- Posted by
- Posted on December 15, 2025
- Computers,IT Support,Printer,Windows
- No Comments.
Restore the Legacy Print Dialog in Windows 11 (22H2) Starting with Windows 11 version 22H2, Microsoft replaced the legacy print dialog for all classic Win32 applications with a new unified print interface. This change also affects applications such as Giza, and for some users the new dialog has proven to be less efficient or more […]
Windows 11 – Quickly Open the Manual Printer Add Dialog<
- Posted by
- Posted on December 12, 2025
- Computers,IT Support,Networking,Printer,Windows
- No Comments.
Windows 11 hides many legacy but extremely useful administrative tools behind modern UI layers. One of these is the classic PrintUI utility, which allows you to quickly access advanced printer installation dialogs without navigating through multiple Settings menus. This is especially useful for IT administrators, MSP technicians, and anyone troubleshooting printer installs, driver issues, or […]
Windows Vista, 7, 8, 10, 11 – GodMode
- Posted by
- Posted on December 12, 2025
- Uncategorised
- No Comments.
How to Enable Windows God Mode in Windows 10 and Windows 11 Windows includes a hidden feature known as God Mode, a special control panel folder that provides direct access to more than 200 advanced system settings in one place. Instead of navigating through multiple menus, God Mode organizes every available configuration option into […]
Restore the original Windows Photo Viewer in Windows 11
- Posted by
- Posted on December 12, 2025
- Computers,IT Support,Microsoft Applications,Windows
- No Comments.
How to Restore Windows Photo Viewer in Windows 11 Many users still prefer the speed and simplicity of the classic Windows Photo Viewer. Although Microsoft did not remove the program itself, the registry entries that associate image file types with Photo Viewer were removed during the upgrade from Windows 10. This is why Photo Viewer […]
How to Skip Microsoft Account Setup During Windows Installation
- Posted by
- Posted on October 5, 2025
- Uncategorised
- No Comments.
During Windows 11 setup, Microsoft now tries to force you to use a Microsoft account to sign in, This can be frustrating for administrators or users who prefer creating a local account instead. One of the most common workarounds has been using the OOBE\BypassNRO command during setup. However, in recent Windows builds, this method doesn’t […]
How to Upgrade a VMware Workstation Virtual Machine to Windows 11 with a Working TPM Module
- Posted by
- Posted on September 24, 2025
- Computers,Virtualization,Windows
- No Comments.
Windows 11 requires UEFI boot, Secure Boot, and a Trusted Platform Module 2.0. If you are running Windows 10 inside VMware Workstation, you may need to reconfigure the virtual machine so it meets these requirements before upgrading to Windows 11. This guide explains how to upgrade a VMware Workstation VM and add a working virtual […]
Recent Posts
- New Chrome Setting Which Blocks Local Network Access for Web Apps
- Creating and Removing Local Administrator Accounts in Windows
- Apple Mobile Device Drivers on Windows
- Controlled Folder Access
- Mac CUPS: The Local Host Printing Interface Explained
Archives
- February 2026
- January 2026
- December 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- February 2025
- January 2025
- July 2022
- February 2022
- January 2021
- July 2020
- May 2020
- February 2020
- December 2019
- August 2019
- January 2019
- July 2018
Categories
- Computers
- IT Support
- Lab
- Linux
- Mac OS
- Management
- Microsoft Applications
- Networking
- Printer
- Router
- Servers
- Switch
- Uncategorised
- Video Conferencing
- Virtualization
- Website
- Windows